In the past few years, Advanced Persistent Threat (APT) groups have seriously stepped up, especially when gunning for financial institutions. Forget cookie-cutter ransomware—these actors are crafting tailored attacks built specifically for each victim’s environment.
Groups like APT38 (aka Contagious Interview / Famous Chollima), part of North Korea’s Lazarus crew, have been using GitHub in wild new ways—targeting developers directly by posing as legit crypto startups offering coding gigs or interviews.
Here’s how the scam goes:
1. You get contacted for a cool dev job.
2. There’s a “skill test” via GitHub—looks clean at first.
3. Behind the scenes? Weaponized backend code, custom-built for your stack.
In one case we investigated (we’re calling it ForexProvider), the attackers shared a full-stack “stock ticker app” built with Next.js, Tailwind CSS, Java, and Docker. It looked great. But the backend had a service hidden code to fetch payloads from a remote server—an open door for remote code execution (RCE) if triggered.
This wasn’t just sloppy coding. It was a smart, modular setup:
• The frontend looked AI-generated but clean.
• The backend contained “second-grade” vulnerable code—nothing obviously malicious unless a bad payload was served.
Key tactics we saw:
• GitHub repos disguised as “skill assessments”
• Backend services hiding in plain sight
• Use of Java deserialization for stealthy RCE
• Obfuscated code and subtle privilege escalation
These campaigns are fast, smart, and designed to bypass traditional defenses. And with AI and crypto profits ramping up, the time needed to pull off these attacks could shrink from 30 days to just 3.
Bottom line: If you’re a dev working in fintech or crypto, beware of random GitHub repos and coding tests from unknown “startups.” These aren’t just phishing attempts—they’re full-blown custom APT campaigns.
APT38, also known as Contagious Interview or Famous Chollima, is a subgroup of the notorious North Korean state-sponsored Lazarus Group. According to Silent Push in a very reach and recent piece of threat intelligence https://www.silentpush.com/blog/contagious-interview-front-companies/#Investigating-BlockNovas'-GitHub-Infrastructure from April 2025, this group has recently launched a sophisticated campaign creating three front cryptocurrency companies—BlockNovas LLC, Angeloper Agency, and SoftGlide LLC-to deliver a trio of malware: BeaverTail, InvisibleFerret, and OtterCookie.
Here we are discussing the case when the code, pushed to the developer, is not generic and well-designed malware but it is code developed to compromise the specific target's environment.
By looking at the frontend, AI generated code really strikes our eyes, but we didn’t identify malicious tricks. Different story for the backend. While it fully implements the HTTP backend to enable the app with CRUD functions on stocks/db, it also installs a service and deploys as a Maven plug in. By looking a little bit more into the code, we were able to spot a service timed that GET for a stock quotation update to a remote backend on the internet.

The response from the public endpoint provides a Base64 payload that later gets deserialized and cast-ed to a java object; that's a pretty common practice, but we are aware of a couple of issues with deserialization in java Below, we compare the PoC exploit code shared by Portswigger (on the left side) with the code in the malicious App on the right side. Long story short, the attacker can trigger code execution within the java virtual machine invoking java internal primitives.
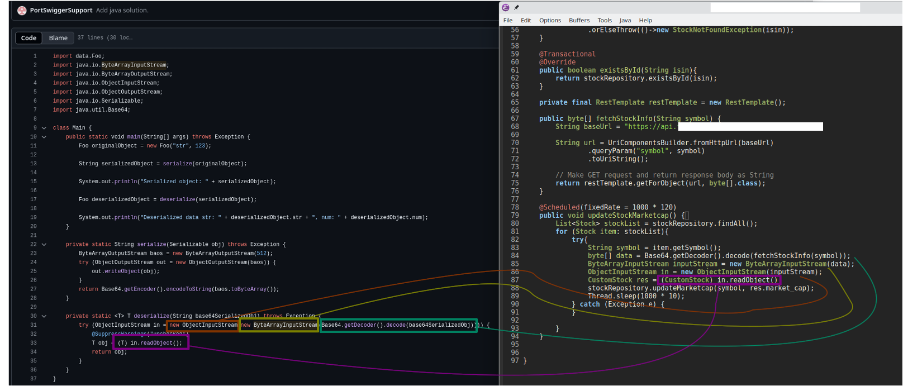
We wouldn’t define it as "bring your own vuln" case, here the vuln is known and just smartly reused. Usually, malicious Apps distributed in the recruitment skills assessments can present:
1. Hidden malicious code: Inserting numerous spaces before malicious code so it renders off-screen in the GitHub interface
2. Obfuscated backdoors: Hiding backdoors in seemingly legitimate JavaScript files (we didn't scout deeply the frontend code)
3. First Grade vulnerable code: straight vulnerable call that invokes system functions or allows the attacked to execute code
4. Second Grade vulnerable code: weak code or use of weak functionalities of the development environment that chained together can lead to execution of code (it’s our case).
Usually, we see advanced malware with stealth capabilities—things like a dropper or stager loading a full payload into memory. But this time? It’s more like a constellation of tiny tools, each doing its own little job. It starts in the Java environment, then breaks out to the operating system, gradually trying to escalate local privileges.
Here’s the attack sequence we observed:
1. The malicious code arrives via a GitHub repo clone—specifically set up for this attack and wiped right after.
2. The main Java executable gets run by the lured developer.
3. Next comes persistence. A malicious .java file (yep, a Java file, not a .class) gets inserted as a plugin into the Maven M2 compiler pipeline—leveraging newer Maven features.
4. It exploits a serialization flaw, using a payload fetched from a remote location, takes control over the java environment, and downloads another PE as a stage.
5. The PE gets executed, we are now out of java vm and landed in the OS, multiple other files get downloaded with names that are recalling legit files, and written in the c:\users\public folder.
6. Then, more files get pulled from compromised support infrastructure—think legit-looking sites and exploit domains with a good reputation.
7. Multiple processes are spawned, UAC bypass and C2 over HTTPs; to achieve that, a file gets downloaded with a XXXXX.db extension that hides a plain win32 DLL with one entry points. Once executed via a proxyloader that bypasses EDR detection, it just become a traditional rundll loader and executes a series of commands in batch contained in a text .ini file. The file name is deliberately chosen to blend in with routine utilities—like docker-build tools—that appear frequently in telemetry and are typically overlooked.
We noted that one of the DB files is available on Virustotal, therefore we performed some reverse engineering on that payload publicly distributed. The rest of IoCs we obtained from the case are restricted to TLP AMBER and will not be divulged in this article. https://www.virustotal.com/gui/file/367c5dcf64310763c74b948c051651962a8295d23f2798fd1ef387c5af773d76/details
The file is a win32 masked DLL, exporting 1 entry and 2 additional functions:

The entry point of the dll goes straight into the execution in batch a series of commands spawning new processes, the core identified routine has been decompiled and renamed as “executeCommandsFromFile”:
The function renamed to executeCommandsFromFile performs the following key operations:
1. Initialization:
- Sets up a security cookie for stack protection
- Initializes a filename buffer with an encoded/encrypted filename
- Allocates various buffers for command processing
2. File Decryption:
- Performs XOR decryption (using key 0x0A/10) on the filename stored in filename_buffer
- The decryption loop processes the filename character by character (see below)
3. Command Processing:
- Opens the decrypted filename in read mode ("r")
- Enters a loop that continues until EOF is reached
- For each iteration:
* Clears a command buffer
* Reads a line from the file into command_buffer
* Initializes STARTUPINFO and PROCESS_INFORMATION structures for Windows process creation
* Processes the command string (removes trailing newline/carriage return)
* Creates a new process using CreateProcessA to execute the command

* Properly closes process and thread handles
4. Cleanup:
- Closes the command file
- Verifies stack cookie integrity
Key variables:
- command_file: File handle for reading commands
- command_buffer: Buffer storing the current command to execute
- startup_info: Windows process startup configuration
- process_info: Process information for created processes
- filename_buffer: Stores the encrypted/decrypted filename
The function appears to be part of a command execution system, possibly used for batch processing or automated command execution. The filename is stored in an obfuscated format and decrypted before use. The caller (FUN_180001300) appears to conditionally trigger this function when param_2 equals 1, indicating this might be part of a larger command processing system.
The filename_buffer is defined as follow:

XOR decryption on the buffer 0x79786f797f563069 using key 0x0A (decimal 10), we XOR each byte of the buffer with 0x0A:
0x79 ^ 0x0A = 0x73 -> 's'
0x78 ^ 0x0A = 0x72 -> 'r'
0x6f ^ 0x0A = 0x65 -> 'e'
0x79 ^ 0x0A = 0x73 -> 's'
0x7f ^ 0x0A = 0x75 -> 'u'
0x56 ^ 0x0A = 0x5C -> '\'
0x30 ^ 0x0A = 0x3A -> ':'
0x69 ^ 0x0A = 0x63 -> 'c'
By keeping going on the rest of the buffer we obtain: C:\users\public\_desktop.ini
TradeTraitor represents another significant North Korean APT campaign targeting the financial sector. According to a joint Cybersecurity Advisory (CSA) issued by the FBI, CISA, and U.S. Treasury Department in April 2022, this campaign is attributed to the Lazarus Group (also tracked as APT38, BlueNoroff, and Stardust Chollima).
TradeTraitor describes a series of malicious applications written using cross-platform JavaScript or Node.js runtime environment. These applications purport to be cryptocurrency trading or price prediction tools, featuring professionally designed websites advertising their alleged features. Our ForexProvider is written in Node and Java, traditional Java targeting a specific toolchain with Maven.
Other cases have been recently observed using similar techniques, such as an “update” function (e.g., UpdateCheckSync()) that:
1. Makes HTTP POST requests to PHP scripts hosted on TradeTraitor domains
2. Uses AES 256 encryption to decrypt payloads
3. Executes the payloads using Node.js methods
The domain was registered and decommissioned within a very short timeframe and was not cached by the WaybackMachine.
There are a few peculiarities that we want to highlight for ForexProvider:
• The infrastructure, including domain registration, was rapidly deployed and subsequently dismantled specifically for the target.
• The attacker demonstrated a high level of confidence in the target development environment, not only leveraging Maven but targeting a specific version and knowing that Docker was installed—information gathered through social engineering during the interview.
• The attack leverages a typical DevOps environment as its target, marking one of our first time seeing an APT actors exploit a Java and Maven setup.
• We see a constant effort to confuse hunters by using files with usual naming convention (e.g. docker-create.exe is actually a proxy to RunDLL)
• The scattered execution over multiple malicious tools create noise and confuse the detection engines
• Advanced additional new tradecrafts identified: compiling on target
With limited confirmation and forensic, we assume the attacker could have compiled artefacts using the C# compiler csc.exe presented on the target machine. That might explain why so many scattered different small tools are avoiding layers of detection and threat hunting. By compiling on target there are great advantages, you are moving text and not binaries, and certainly a big part of traditional IoC based detection would fail to identify the newly (and unique) created executable.
These campaigns demonstrate a clear evolution in sophistication over time and speed of execution: Faster compromise-to-action timelines, sometimes within a week or 3 days in our specific case, from the interview to crafting a completely malicious targeted application and deliver the attack.
To protect against these sophisticated GitHub-based attacks targeting developers, organizations should implement the following measures:
1. Developer security awareness:
o Train developers to recognize suspicious GitHub repositories and job offers
o Implement strict code review processes for external dependencies
o Verify the legitimacy of companies before engaging in interviews or assessments
2. Technical controls:
o Implement application allowlisting to prevent unauthorized code execution
o Deploy endpoint detection and response (EDR) solutions
o Use software composition analysis tools to identify suspicious dependencies
3. Organizational policies:
o Restrict use of company-issued computers for personal activities
o Implement strict verification procedures for new hires
o Establish secure development environments with limited access
o Regularly audit GitHub and other code repository access
• Perform regular threat hunting
Especially with these new attacks, threat hunting has become extremely relevant. Making hypothesis-based investigations and looking for indicators like those presented within this article has been proven very important to identify and either prevent those attacks:
• Monitor for suspicious cloning of unusual GitHub repositories and consider rating these repositories based on their security and reputation. Using tools like Microsoft Sentinel or Microsoft Defender for Endpoint (MDE), a straightforward query can serve as a starting point for deeper investigations and help identify users cloning potentially unsafe repositories on corporate devices:
DeviceProcessEvents | where Timestamp > ago(7d) | where ProcessCommandLine contains "git" and ProcessCommandLine contains "clone" | where ProcessCommandLine !contains "<put here your corp github name>" and ProcessCommandLine !contains "com.microsoft" | project TimeGenerated, AccountName, ProcessCommandLine | summarize count() by ProcessCommandLine | sort by count_ desc
• Observe mail delivery logs to identify recruiters approaching targets on Corp email addresses, from LinkedIn, which doesn’t look appropriate or compliant.
• Identify abnormal use of the DevOps environment by detecting commands that appear legitimate but do not occur across the entire developer group. Develop a profile of “normal” behavior to spot anomalies within the team. While this is a challenging task, it can be accomplished by implementing sophisticated threat hunting using notebooks (e.g., Jupyter notebooks). We plan to publish a detailed article on this approach soon.
• Identify common looking executables running out of their usual and legit folders (ex. edgebrowser.exe in a public writable folder)
• Monitor for instances of csc.exe (the C#/.NET compiler) executing unusual compile commands, especially when launched as a child process of non-console applications (for example, a Java process or Maven invoking csc).
The targeting of developers through GitHub infrastructure by AP38, TradeTraitor, and other North Korean APT actors represents a significant evolution in the threat landscape. By focusing on developers with privileged access to critical systems and code repositories, these threat actors can gain initial access that leads to devastating breaches and financial theft.
The speed at which these groups operate registering domains hours before attacks, compromising systems within days, and adapting to freshly obtained intelligence from developer interviews makes them particularly dangerous adversaries. Their sophisticated use of GitHub, professional-looking front companies, and elaborate social engineering demonstrates a level of preparation and resources only available to state-sponsored threat actors.
As these campaigns continue to evolve, organizations in the financial sector, particularly those dealing with cryptocurrency and blockchain technology, must remain vigilant and implement comprehensive security measures to protect their developers, and perform Threat Hunting to identify ongoing attacks and variation of similar tradecrafts.
References
1. Silent Push. (April 24, 2025). "Contagious Interview (DPRK) Launches a New Campaign Creating Three Front Companies to Deliver a Trio of Malware: BeaverTail, InvisibleFerret, and OtterCookie." https://www.silentpush.com/blog/contagious-interview-front-companies/
2. Palo Alto Networks Unit 42. (November 21, 2023). "Hacking Employers and Seeking Employment: Two Job-Related Campaigns Bear Hallmarks of North Korean Threat Actors." https://unit42.paloaltonetworks.com/two-campaigns-by-north-korea-bad-actors-target-job-hunters/
3. CISA, FBI, & U.S. Treasury Department. (April 20, 2022). "TraderTraitor: North Korean State-Sponsored APT Targets Blockchain Companies." https://www.cisa.gov/news-events/cybersecurity-advisories/aa22-108a